What are VPNs?
Published June 8, 2023, 11:20 a.m. by Naomi Charles
See this entire course on the Intro to Cybersecurity playlist. https://cbt.gg/2DEq4L6
Ready for the Cybersecurity quiz? Take it here. https://cbt.gg/2DyZeFg
Virtual Private Networks (or VPNs) secure data as it passes across public or shared networks. CBT Nuggets trainer Keith Barker explains how VPNs improve privacy and security when communicating over a network.
What are Intro to IT courses?
We all have to start somewhere. Intro to IT courses allow aspiring and seasoned IT pros alike to explore the different corners of the IT career field. These free, open courses are taught at a level anyone can understand by the same great CBT Nuggets trainers.
Step 1: Watch this entire course. If you watch the course, then the quiz will be a breeze.
Step 2: Test your knowledge with the 7-question Intro to Cybersecurity quiz. Good luck! https://cbt.gg/2DyZeFg
Step 3: Earn the Intro to Cybersecurity Certificate of Completion.
Step 4: Continue learning cybersecurity with CBT Nuggets.
Watch all the Intro to IT courses: https://cbt.gg/2Hy2Qey
You may also like to read about:
when two people are having a private
conversation they expect it to be
private to have confidentiality for what
said back and forth well if we're
sending sensitive information over our
networks we also want privacy and
confidentiality for that information
that we're sending back and forth and
one great tool that we can put in our
Batman tool belt the help enforce and
provide confidentiality for data as it
goes across our networks is a virtual
private network of VPN and that's what
we're going to take a look at right here
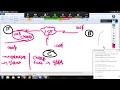
in this video so let's use this network
topology as a backdrop for our
conversation regarding Virtual Private
Networks and let's imagine this site on
the left here is the headquarter site
and over here we have the branch office
and we've got Bob right here
at the headquarter site and to get
connectivity between the branch office
and the headquarter site they are
leveraging the internet for connectivity
so when Bob sends packets in traffic to
a server over at the branch office that
traffic would go something like this
through the routers through the firewall
through this router through the internet
and all the pieces there and finally end
up at the branch office and at the
server data and the challenge is is that
if there's an eavesdropper anywhere in
that path who is listening to the
traffic they can copy that traffic and
if it's not protected with encryption
they can go ahead and make sense of the
data so if there are sensitive
information going between Bob and the
server of the branch office we've just
ruined confidentiality because the
eavesdropper now has access and can make
sense of that data so one of the
solutions that we can use is to use
encryption and we've touched on this in
a previous nugget but encryption is the
concept of scrambling the data in such a
fashion so that if anybody gets a hold
of it without the right keys to unlock
that data or decrypt that data it's just
a bunch of gobbledygook so the attacker
are the eavesdropper on the internet
eavesdropping on our traffic if it's
encrypted they can't make sense of it
and it's of no value to them so a
question might be well how do we make
sure that all of our traffic is
encrypted well we have a few options
there we have some applications if we
pulled out our smart phone and we are
using a messaging app or some other app
it's very likely that individual
applications are doing encryption before
they're sending data back and forth
between your mobile device and some
other device so the apps could implement
encryption
on their own however the problem is that
that's not going to cover everything
that's going into and out of your phone
over for example a Wi-Fi connection case
in point if Louis with their mobile
device opens up something that runs
telnet telnet is a an application that
can be used to remotely connect to
another system and it's not encrypted so
if Louis opens up a telnet application
that's not encrypted and she starts
communicating over a network that
traffic is then subject to eavesdropping
and the attacker could learn sensitive
information like usernames and passwords
and anything else that the attacker
captured as Louis was communicating
using a protocol a set of rules if you
will that didn't include any type of
confidentiality or encryption so another
answer to the question how do we protect
and encrypt everything would be we could
use a virtual private network and with a
virtual private network everything that
goes to the network adapter once the VPN
is turned on everything is encrypted as
it goes through so if we wanted to
provide confidentiality in encryption
services between everybody at
headquarters office when they talk to
the branch office and vice versa
we could implement our Virtual Private
Network and maybe we put it up the
firewall so that is one end of the VPN
tunnel just to refer to as the path for
the virtual private network and ok to
have that VPN tunnel go from the
firewall all the way up to another
device maybe they have another firewall
up at the branch office up to here
so with this VPN tunnel established
between the firewall at headquarters in
the firewall at the branch office now
Bob over here when he sends traffic it
would go through the switches through
the routers hit the firewall at that
point it would be encrypted and put into
this logical VPN tunnel this VPN path
that goes between this firewall and that
firewall so anybody eavesdropping
anywhere in the tunnel
all they're gonna get is gobbly
because they don't understand how to
decrypt the data the eavesdropper is
known and then once it hits the firewall
at the branch office the firewall there
decrypt it and then it passes it on to
its final destination so if Bob was
talking to a server that's gonna be
transparent to Bob all Bob knows is that
he's communicating with the server and
the firewalls are providing both ends of
the tunnel for the encryption and
decryption respectively now this type of
tunnel that's going between two sites
our branch office site and our
headquarter site it has a special type
of name when we're
connecting two sites together with a
tunnel and it's referred to as a
site-to-site VPN so whenever you hear
the term hey we've got a site-to-site
VPN it just means that there's two
devices one at each end between two
sites that are encrypting and decrypting
the data so it can securely cross over
the network and not be vulnerable to
eavesdroppers but wait there's more
another type of a virtual private
network of VPN that we can build is
referred to as a remote access VPN it
would go something like this we have a
user and let's say that user is on the
internet and let's call that user Larry
so Larry is on the Internet maybe he's
at his home at a hotel and Larry would
like to access a server or some other
resources at the headquarter site but
all he has is the internet to go ahead
and cross to get there so we don't want
to have Larry communicate naked Lea over
the internet because then that traffic
would be subject to eavesdroppers so a
solution is we could have Larry built a
VPN from his computer and build his own
VPN tunnel from his own location all the
way to the edge of our network in this
case we're in have our firewall acting
as the head end device for the VPN so
Larry's computer would have a client or
an application that could build that VPN
tunnel from his device to the
headquarter site and then everything
that goes between Larry and the
headquarter site would all be encrypted
and protected from eavesdropping because
of that VPN tunnel and when an
individual computer could be a mobile
device or a laptop when it build a VPN
tunnel to ahead in site that's referred
to as remote access VPN and when the
benefits of that again is we're
protecting we're encrypting all the
traffic as it goes from Larry's machine
through the VPN tunnel and his computer
his device all the way to the other end
of the VPN tunnel in this example it's
the firewall in this nugget we've
learned about a couple different types
of VPNs and the value they bring to the
table and that is to encrypt data
so anybody eavesdropping on that data
won't be able to make sense of it and
that helps keep our data secure I hope
this has been informative for you and
I'd like to thank you for viewing