VPN Split Tunneling: The Benefits and Risks
Published June 1, 2023, 9:20 p.m. by Monica Louis
Learn about the benefits and perils of SSL vpn split tunneling and the reasons why organizations might choose to deploy. We also explain what Microsoft recommends for the o365 use case.
Learn more about this solution at: https://community.f5.com/s/articles/vpn">ssl-vpn-Split-Tunneling-and-Office-365?page=2
You may also like to read about:
[Applause]
[Music]
[Applause]
I'm Peter and welcome to another edition
of f5 Dev Central's lightboard lessons
with many organizations rolling out VPN
solutions for their remote workforce one
of the hot topics these days is whether
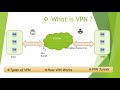
or not to use split tunneling so what is
split tunneling well if we have our
individual working from home they have
their normal internet connection from
their local provider now within their
home network it might be like a ten ten
dot X dot X and then they have their
public IP going to the internet when
they connect to a VPN solution and let's
just draw this over here this would be
corporate now I'm not saying all VPN
controllers are within the confines of
the corporation but you get where I'm
coming so the VPN so when they when they
connect to the VPN they got obviously
authenticate and do whatever you know
device inspections what-have-you and
they're when they when they hit that VPN
obviously they're going out there public
internet connection to the VPN and once
they authenticate the VPN then creates
an encrypted tunnel using SSL or TLS now
if you look at your network adapters
here you have your ten dot but what will
be added to that would be what's called
a PPP adapter a point-to-point protocol
adapter and it
I was a protocol to use the existing
interface and then that adapter will
have an address often it's like 172 or
whatever the corporation's using and you
can see all this in your IP config once
once you connect to the VPN you now have
your regular internal network and your
public IP address but you then have this
other IP address noted as in your IP
config and often it's not always but
often it's a PPP adapter and so this is
TOS so this is the encrypted tunnel but
obviously everything is still going over
the Internet
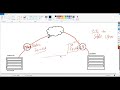
now what split tunneling is is so a lot
of organizations have once you're
connected to the VPN anything that goes
to the Internet whether its corporate
bound resources so any internal
resources here or just you know search
terms going to Google or checking Amazon
or anything like that
often that VPN that all that data will
go through this connection and then out
to the internet from the VPN itself
now the reason organizations do that is
oftentimes they'll have like a DLP
solution here or forward proxy some sort
of filtering mechanism or ensuring that
nothing is leaving that it shouldn't
leave so it's a security mechanism here
by having everything push through the
tunnel and out again what split
tunneling is is essentially saying that
only traffic that is destined for the
corporate network will go through the
tunnel anything else anything publicly
available will go out through this
connection and so the topic really is
like should you or should you not do
split tunneling now the problem
or what happens is now that there's more
people working from home and coming over
the VPNs a lot more traffic is getting
pushed through this way rather than
going out this way and so it can create
a bottleneck here and sometimes the VPNs
and other devices that are within there
can't handle the traffic so what
organizations do is they enable split
tunneling so the public stuff goes out
your public and then the corporate dust
and stuff goes through that way and
prospectus 365 so why don't we just put
ou 365 down here but you know they're
all connected often people would push
everything through here to then get to
office 365 Microsoft is actually
suggesting to do split tunneling so for
things like team SharePoint what have
you still do authentication but and
reverse proxy it but send them out
through the split tunnel so the risks
here now yes you're certainly reducing
traffic hitting that way by allowing
just a normal search and other public
traffic to go out that way but obviously
the risk here is is the accidental
disclosure or or information that might
be here that would have been caught with
the forward proxy DLP or firewall on
this end accidentally slipping out
there's also solutions that'll you know
check to make sure that your going
through are going to the proper office
365 installation since Fisher is out
there are using what real good-looking
office 365 kind of authentication looks
to to kind of trick people into putting
their credentials into a fake phishing
office 365 sites so there's definitely
risk on that but that's essentially what
split tunneling
is and why you might want to or not want
to do it you definitely save bandwidth
with split tunneling and save resources
within the corporation during this time
but the risks of course are by not
pushing everything through the tunnel
and checking it before it goes out
it's just that potential of maybe
getting to fishing after office 365 site
or or potentially sensitive materials
getting getting sent out through the
public internet unencrypted without
going through the inspections if you'd
like to learn more about split tunneling
office 365 by the way f5s VPN solution
is access policy manager you can visit
us at def central dot f five.com
if you liked this video please hit the
like button and subscribe if you haven't
already
i'm peter thanks for watching and we'll
see you in the community oh I forgot to
sign my work always sign your work
you