Day 3-Zscaler Architecture Deep Dive, Understand Zscaler Elements-Control Vs Data Vs Statistic Plane
Published July 9, 2023, 8:20 a.m. by Naomi Charles
Get Full zscaler Course Access (zia and zpa), Please connect on below Contact:
◆ WhatsApp/Call for Enquires → https://wa.me/919289682701
Looking to upgrade your skills in networking, security, and cloud networking? guinet Technologies offers live training sessions with 24/7 lab access to help you achieve your goals. Our courses are taught by experts in the field and cover a wide range of topics, including CCNA, CCNP,CCIE IE, SDWAN, Palo Alto, Check Point, FortiGate, Cisco ASA, and cloud networking. Don't wait - Enroll now and visit our website to learn more about our courses.
◆ Visit our website →https://www.guinett.com
◆ WhatsApp for Enquires →https://wa.me/919289682701
◆ Download guinet Mobile App →https://play.google.com/store/apps/details?id=com.guinet.learners
◆ Join Our Telegram →https://t.me/+uG71yFVxMXo2NGNl
◆ Join Facebook Page →https://www.facebook.com/GuiNetTechnologies
Cisco Courses:
=============
◆ CCNA 200-301
◆ CCNP Enterprise-ENCOR
◆ CCNP ENARSI
◆ CCIE IE
◆ SD WAN (Cisco SDWAN & Versa SDWAN)
◆ CCNP Data Center
Firewall & Loadbalance Courses:
==========================
◆ Palo Alto Firewall
◆ Check Point Firewall
◆ FortiGate Firewall
◆ Cisco ASA Firewall
◆ Shopos Firewall
◆ F5 LTM Load Balancer
zscaler Courses:
==============
◆ zia-zscaler Internet Access
◆ zpa-zscaler Private Access
Cloud Courses:
============
◆ Azure
◆ AWS
◆ GCP
zscaler
zscaler client connector
zscaler vpn
zscaler private access
zscaler application
zscaler internet access
zscaler cloud
zscaler client connector download
zscaler cloud connector
zscaler products
zscaler gartner
zscaler overview
zscaler application connector
zscaler client
zscaler pac file
zscaler trust
internet security by zscaler
zulu zscaler
zscaler for mac
zscaler what is it
zscaler security
zscaler company
zscaler okta
zscaler connector
zscaler zcc
zscaler ipv6
zscaler magic quadrant
zscaler data protection
zscaler client download
okta zscaler
zscaler download for windows
zscaler sse
zscaler cloud security
zscaler remote access
zscaler what does it do
zscaler web filtering
zscaler web security
zscaler privileged remote access
zscaler for users
zscaler application download
zscaler download windows 10
trust zscaler
zcc zscaler
zscaler azure
zscalertwo
zscaler microsoft
zscaler cloud protection
download zscaler client connector
zscaler cyber security
zscaler advanced threat protection
zscaler services
zscaler solutions
zscaler integration
pac file zscaler
zscaler vpn download
vpn zscaler
zscaler analyzer
zscaler meaning
zscaler mac download
zscaler macos
zscaler vpn client
cloud connector zscaler
zscaler for mac download
zscaler what is
zscaler download windows 11
sitereview zscaler
zscaler client connector download windows 10
zscaler download windows
zscaler pac
about zscaler
zscaler always on vpn
zscaler and okta
okta and zscaler
zscaler ticket
remote assistance zscaler
zscaler windows download
download zscaler windows
zscaler client connector download mac
zscaler for windows
zscaler download for windows 11
zscaler client connector for windows
zscaler macos download
download zscaler for windows 10
zscaler client connector download for windows 10
use of zscaler
download zscaler for mac
about zscaler company
download zscaler client connector for windows
zscaler technology
zscaler client connector windows
zscaler client connector mac
zscaler syslog
npm zscaler
zscaler linux download
zscaler client connector download for windows
zscaler windows 11
pac zscaler
fortinet zscaler
zscaler learning
privileged remote access zscaler
velocloud zscaler
zscaler vpn download for windows 10
intune zscaler
zscaler private access download
zscaler no internet access
zscaler server
zscaler client download for windows 10
zscaler internet access pricing
download zscaler client
zscaler active directory
zscaler websocket
zscaler analyzer tool
zscaler azure ad integration
zscaler backup and restore
zscaler cloud connector azure
zscaler cloud native platform
zscaler kerberos
zscaler remote desktop
zscaler mtr
zscaler connector download
zscaler vpn client download
zscaler sitereview
zscaler monitor employees
zscaler platform
zscaler work from anywhere
zscaler access
zscaler is a vpn
zscaler total employees
aws marketplace zscaler
zscaler anyconnect
client connector zscaler
zscaler mac client
zscaler 100.64
zscaler web
okta zscaler integration
zscaler client connector mac download
zscaler web isolation
internet security zscaler
zscaler private access connector
zscaler udemy
zscaler private access pricing
web insights zscaler
zscaler cloud connector aws
zscaler client connector download for mac
zscaler how does it work
zscaler palo alto networks
zscaler info
zscaler network security
zscaler is vpn
private access zscaler
zscaler traceroute
zscaler site to site vpn
zscaler how to use
zscaler and vpn
zscaler private
zscaler windows 7
zscalerbetazscaler cloud security platform
zscaler infrastructure
zscaler information
learn zscaler
zscaler pcap
You may also like to read about:
hi everyone welcome to winner
Technologies right and today we are
going to start our
z-scaler architecture right uh module
earlier we discussed a few things about
the basic of the GS color product
overview right and in this module we are
discussing about the G Square internet
access I hope you guys watched my
previous videos where I explain about
everything what is my G scalar internet
access what images the private access
what is my jdx so we'll discuss in very
detail and also we just briefly
understand about the products so I hope
you guys go through that and you
understand that and then we understand
about the G Square platform what is a
control plane data plane and the login
plan status plane and we try to
understand about the gene what is the G
Square enforcement node little bit and
how the policy can be driven with the
help of the uh our Central Authority
that is again a new things we have right
and Gia uh Public Service age and Jane
we understand log routers we still have
to understand and the static display we
understand and how user is going to be
connected from the branch offices to the
any Gia and why they are going to
connect I believe you having a little
bit idea and what does means zero trust
exchange so these all already we have
done the discussion in the previous last
two lectures but now
we are going to understand
G is scalar architecture or that is
limited to the G scalar Gia
so we are going to understand G scalar
internet
access basically architecture right
so we'll do the Deep dive what is a g
scalar internet architectures and how it
looks like
and in addition of that also we have uh
discussed more about like module agenda
like what is the elements of the gscaler
clouds right
single skin multiple action that is a
ssma and traffic forwarding and
authentication methods like this is a
high level we'll do the very deep level
discussion in the later stage and it's a
high ability so we'll try to explore
each and everything step by step we'll
try to understand so let's start so
first we try to understand what is g
scalar elements GS Cloud G Square
elements so don't be confused about the
products and elements right so I
explained previously about the product
spread form these are the completely
different things but when I talk about G
scalar elements that is a completely
different things right and then we'll
understand about the ssma single scan
multiple actions and traffic recording
methods uh like uh over will understand
the overview like can you do the
specific deep dive for the all traffic
forwarding method authentications and
many more and high ability everything
right
and configuration building
troubleshooting actual overview
everything will understand
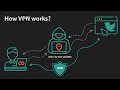
so let us start so you guys see here one
of the diagrams right and if I am
showing these diagrams what basically
yours come what's basically question
coming in your mind so you can see a lot
of pictures admin console Global console
Samuel ldap Splunk users like they're
having a gen so gen is equal to G scalar
enforcement node so see here 10 is equal
to G scalar enforcement node so you guys
can write it down different different
terminology might be you are seeing in
the first time you see the central
authorities you might be write this word
also right you might be write down the
samples right this is the first time
admin Global console this is the first
time this internet is common right and
you can see here we having the log
routers also right so we having a
different different scenarios right and
based on the different different
scenarios we are using different
different component and elements so
these are basically elements so Central
Authority is one elements GI Jane is the
one element right G scalar enforcement
node is one Element saml also that is
the one Services behind uh this element
that is going to mandatory use console
admin console is also going to be used
right your log router is also going to
be Nano log policer also going to be
used even Nano logo streaming services
also so these all are very relevant for
you all right so if you're just
understanding this particular solution
so probably you have to understand each
and every component right so I hope uh
just you guys write down about the
different different elements Now
understand what is the use of this
elements and why basically we are using
these elements right so
basically whenever we're just going to
start G scalar right so we having a
three planes right so when I say three
planes what does mean the three planes
so let me just just now open my
and how this elements are coming a
picture while defining the three planes
so let me just open it uh it's taking a
little bit longer time but let me see if
it is going to be openable soon
so
Let It Be
all right
so the same agenda I have just you know
written here because the architecture
and all so what this means like why
before I am going to explain this all
planes before I going to explain these
all elements and all right so you just
have to understand some prerequisite and
Concepts which is very important for you
so before I go and start explaining the
G Square element you should know how my
router how my firewalls works and what
planes they have because G scalar you
can see here they are talking about the
elements having a three planes control
plane data plane static display so do we
have the similar step in my routers do
we have similar steps maybe the switches
do we have the seamless steps or like
functionality in my firewalls the answer
is exactly yes you keep using these
planes in your routers your firewalls
your switches or any other networking or
security devices
so if I'm giving the examples if I'm
giving the example control planes what
is the control plane so if you're doing
the if I'm talking the router and
example any routings like ospf right if
you are using the bgpm right
if you're using the any routing protocol
like repl anything is static routing
they all are there part of the control
pins that means they are giving the
instructions and without instruction you
cannot switch the packets
you cannot switch the packets if you
want to switch the packet from one
interface to another interface basically
you just have to use this particular
control plane device
or device control pin intelligence right
so
routing is going to instruct how
basically you know uh you have to you
know uh choose the exit interface right
based on the packet arrive in your
device so these are the control plane uh
like protocols like ospf
we having the bgp right we having the
eigrp or might be the rip or any other
protocol you can just select it
what is the data plane right so data
plane is nothing like the Ingress or
increase interface means if packet is
landed from this interface and going to
out this interface right so maybe this
interface is ethernet 0 by 0 right and
this is a ethernet
0 by 1 so the moment the packet landed
to me and taken consultation from the
control plane and then finally they
decided I just have to go this packet
out that is a data plan means where you
just transfer the data from one
interface another interface so these are
the two primary component you just have
to use in any router any firewall any
switches
and then what is the statistics plane
so if we want to monitor this router
remotely you want to see what is my
interface status right
you want to check my any bgp neighbor
went down or up right ospf neighbor
status right any SNMP based monitoring
like any health monitoring device
monitors CPU monitoring solar wind you
just want to integrate any other
interface monitoring interface goes down
up any protocols there's all going to be
monitored that who is going to provide
that strategies that is a again we have
in the different different tools are
coming different different like most
common is the SNMP protocols you just
configure and based on the MIB and the
SNMP settings they keep calling the
devices information by the tools like
with solar wind and we're having the
snow tools a lot of tools available in
the market and you just monitoring so
that is the Statics they are going to
provide the device health status device
real time status what is happening my
device all traffic status how traffic
what is the bandwidth utilization
circuit utilization everything you are
doing that
so this is something we keep using the
same thing right
but if I talk about what is the
relevancy of this particular three
planes for G scalar see yes we have we
have so again G scalar having a three
planes we're having a control plane
we're having a data plane and we're
having this Statistics plane right and
my dear friends so if I talk about what
is the data plane what is the control
Pane and what is the statistics pane so
probably you just have to understand if
I talk about anything about the control
plane that is something
not similar to the routing but you just
think about just think about your user
ID right
your
organization ID right
your location right your like device
devices right
so we're having a lot of you know based
on the you know user ID location ID
Company ID even even Company ID
Company ID
so
policy even the policy you're just going
to configure policy uh policy info like
whatever you just configure based on the
user right so this policy intelligence
right
so we're having a lot of you know Etc
we're just having I just given the most
common usual examples right so these are
the basically similar to the routing
protocols just correlate these are the
basically G scalar ospf bgp and other
routing protocols
so if you want to based on the user ID
you want to switch the traffic or switch
the data plane you can do that based on
the organization ID you want to do that
you can do that right and based on the
company ID
you want to do something you can do that
right so this is something you just have
to understand how basically the control
pane of the G scalar and how basically
control plane of the routers are
differed to each other so basically they
differ in term of the the way of working
so we are not using any routing
protocols we are not reaching any
switching concept but yes we are using
the real-time organization name user ID
device look device informations Company
ID policy whatever going to and based on
that we can making the intelligence in
the geoscalers
I'll more explain how it is going to
work about right but just think about
the control pane is nothing it's like
the company ID so you can if you go here
in the in my slide you will find the
more information right so if you see the
control panels the control planes right
the brain and nervous systems that
manage the entire Cloud maintained list
of the users see here groups Department
each of the unique ID maintain all of
the policy and the configuration for the
company located in three to four data
center disaster recovery so what is the
three to put data center I'll explain so
if I talk about the control pane right
so control plane is nervous system brain
of the G scalar and without this brain
of the gscaler you cannot do any kind of
the packet processing
so your packet is going to process based
on the your department ID your user ID
your group ID your unique ID policy
whatever you're going to configure they
all are going to connect and in case of
the any disaster is going to happen for
the one of the control pane they are
going to shift automatically to the
another data centers they having a lot
of data center across the globe so I
hope you understand about the control
plan and it's a very important guys
trust me this control pane you must know
how why I just explained the routers and
routings because you can correlate
you can correlate why ospf why ajrp how
they are going to make an intelligence
similar how user ID device ID
organization ID location ID Company ID
policy is going to make in my
intelligence okay so this is your actual
control pin
similar if I talk about data plane here
my friend so data plane is nothing they
are the genes so you see this is the
Gene g scalar enforcement node so Public
Service age or Jane you just think about
the same
so your packet need to be switched so
let us suppose your packet arrived let
me just clear it your packet arrive in
particular user to the gene they have to
go on internet so your packet arrive
from that interface these are the all
physical devices also across the globe
data center is something what
they are the cloud but still they having
the data centers okay so don't be
confused cloud is nothing something
hanging in here okay these are real
devices but they are known as a cloud
because they are centrally located and
they have a very robust communication
very high capacity high performance
devices there so devices are going to
receive the packet that chain or public
services are going to receive the packet
and they are just going to do the
processing with the help of the brain
brain is the control pain and that brain
is known as the central Authority right
so again here see the brain is basically
known as the control pin is known as the
central Authority so here you can see
that Central Authority if you see the
words one of the element this Central
Authority is nothing this is the brain
of the G scalar okay so if you want to
perform the control planes the user must
consult to brain user must consult to
brain If brain allow then only it is
going to redirect to the chain right and
then Jane is going to make a successful
connection with the internet so this is
the core concept guys we are not going
to discuss about the more in deep but
high level because people are very
confused about that how the traffic flow
is going to happen so in in high level
let us suppose take this is the brain of
the router and you want to go on the
internet so you just your PC must go to
the router as a gateway address a router
will check the you know based on the
destination their routing tables based
on the ospf bgp or a static routing
right and based on checking this static
routing they will tell you the what is
the next hope to go to the Internet
similar way
in this particular G scalar Central
Authority which is known as the brain
nervous system control plane Central
Authority is known as the cloud Central
authorities the brain nervous system it
is responsible basically how packet is
going to be switched if the certain
routing parameters similar what routing
parameters we have to match here we just
have to match the group ID Department ID
unique ID policies whatever they have
configured and according to that they
are going to process so your control
plane is Central Authority we just
responded to do all kind of checks and
processing the packet and your chain is
acting as a data plane where gen Zen is
z scalar enforcement node is the highest
speed inspection in the policy
enforcement connecting identify only by
user ID single scan multi-actions
traffic inspection in the body right
traffic process in the memory is never
right today this is the Masterpiece from
the G scaler trust me guys
so while doing the traffic processing
while doing the traffic processing for
the data planes
your traffic never rides in the disk
never write in J scalar disk it is
always right in the memory and from
memory it is going to be processed once
processing has been done memory has been
free
so even the hiker wanted to you know
hack your traffic inspect your traffic
and do something they never going to do
that because you are never going to put
something in the storage storage point
of view not in your hard disk so see let
us suppose I want to steal something
from your uh house so it's easy for me I
can steal something from a house I can
break your lock I can go inside and I
can you know get some you know out from
your house but I want to steal something
from your mind and you don't want to
tell then how it is possible unless even
you kill me or you can just damage my
mind still you cannot get the
informations because something in my
mind so this is the Masterpiece when
doing the data processing while doing
the data switching whenever the process
they always process that traffic
forwarding in the memory never return to
the disk right never written in a disk
so if it is not going to return it is
nobody is going to hack right so this is
a data plane chain of the G scalar right
so I hope you guys understand the
control Pane and you understand the data
plane just let me know in case if you're
watching in the YouTube or somewhere
else or my you know official website
just write an email if you're having any
query I'll help you to clarify on that
right but this is very important just
correlate about this routing again this
is a very important now we're left with
the static display
so why this Aesthetics plane is very
important again
in router I explain you have to monitor
you have to check the health you have to
mount the circuits and everything then
you need to start to explain so if you
want to monitor each and everything so
you require the strategist plane for the
router point of view switch point of the
following point of view similar in the G
scalar if you want to scalable reporting
you want to analyze the loggings and you
want to make the you know any kind of
report just showcase your management
just analyze and check how my health is
working how my device is working and you
want to like log like you want to view
the logs and everything then it is going
to help with the help of the starting
screen the all reporting all information
is going to pull and they are just going
to provide the high visibility right so
this is how Statics plane is going to
work so these all are basically for the
locks okay so I hope you understand so
now let me just go back again to the G
scalar element about the architectures
so if I am going to just element
architecture so you can see here in this
architecture
let's assume this is the users right and
this user wanted to access the internet
so let me just draw here so might be we
just having this
uh might be here is the or by the way he
wanted to access here google.com
oh sorry let me write here so he might
be access google.com so this is a
google.com posted here
so once this is going to be you know
initiate the connection to access this
Google.com so again I'm giving the
overview high levels you just understand
later we'll discuss the low level in in
upcoming lectures so first thing this
user must be you know authenticated
this user having their laptop right this
laptop having the G scaler you know GCC
app should be installed
even that is not going to be installed
there is another way we can just use
that but just think about or just for
time being this problem not be confused
simple make it simple okay so let's this
is a client and want to access the
google.com and sitting in the office so
what they are going to do
first they will authenticate with the
saml level right this is the owner of
the recommended authentication method in
the you know G scalar so once the
authentication is going to happen they
will basically
try to reach right try to reach G scalar
gen
and after reaching the g-squito gene
they will try to contact Central
Authority for the control plane
informations
so Central Authority basically is going
to verify the users right
hey user XYZ you come to me then it will
check for this XYZ user do we have any
kind of the policy allowed to access the
google.com
or this is the valid user basically who
should access the google.com
his company ID is valid his department
is values he's a group ID is valid his
organization ID is valid so this all is
going we can see what the parameters we
have don't have routing we have these
all parameter Department group user list
Company ID unique ID and based on that
basically they are going to
you know
validate users and after validating they
will say okay we are fine to you know
send the traffic so once they authorize
them they enforce the policy and provide
the connection ID then they basically
race to the Gen and Jane
you know start doing the processing the
traffic and this processing never is
going to be written in the Gen disk they
always process in the memory this is the
Masterpiece again I'm repeating okay and
based on that your connection The
Intercept your connection and based on
you if everything is fine they initiate
the connection toward the google.com
and once the google.com is going to
reply you they again
reply
back to you so this is how it is going
to work right so basically Central
Authority is going to basically provide
the complete visibility about the users
what application what kind of the like
Company ID everything and then Jane is
going to just you know forward the
traffic to the any kind of the internet
access on behalf of you and you just
have to you know no need to worry about
your IP address Nat and everything
that's simply going to the Jain and Jane
is going to forward the google.com
yahoo.com whatever you want to go and
then it is going to happen
now
two things we understand very high level
one is for the
gen and one is the central Authority
connection now how they are going to use
or leverage the
GCC or sorry G scalar started to explain
right
so in gscale Aesthetics then what is
going to happen they basically going to
you know help to because they are
processing more than 300 trillions and
billions and billion traffic on a daily
basis right daily basis they are doing
so it's very hard to you know
manage the locks for those you know real
time blocks because a lot of customers
are using the G skillers so it's very
hard to manage those locks so how the
logs is going to be you know manageable
right
so log is going to management in term of
this way
whatever logs we are going to receive
right whatever logs we are going to
receive uh from the any processing point
of view right so the G scalar basically
the G Square basically going to
like like compress the locks how it is
going to compress 30X log is going to be
compressed so whatever the logs you are
just sending you just think about you
just making the size lower than right
whatever the actual value why the helper
30X so we're just mining the logs by 30X
and then with the help of the log router
so every regions every location they
having the log routers right and they
are just sending those location to the
log routers and further your log router
is basically by the help of the log
router you can maximum store the logs
right you can maximum store the logs for
the six month as per the gscaler policy
not more than that okay and you're
already by the using the van
optimization whatever the logs you are
receiving you're just making this
smaller by the 30X right so you're
already doing this 30X compression by
the band optimization and then you can
use and retrieve those retrieve those
approves six months but still right
still you want to analyze or save your
logs in your company local database
right if you want to do that in company
or local database still you having a
freedom to do that so there is a feature
called right there's a nano log
streaming so why an analog so Nano log
routers basically these are the nano log
clusters so they make the Nano log
cluster so different different religions
like we having the emea USA APAC private
so all basically keeping the logs in the
cluster so if anything is goes down
anything is like a disaster happening so
basically other logs other cluster
region having the logs information
and you want to stream those logs
information for my company point of view
in my data center my network so I have
to use the Nano log streaming services
that is an analysis and by using the NSS
Services I can just you know by the help
of this Splunk I can retrieve all the
logs and further I can store as per my
needs six month one year two year
whatever I want to use so this is how
basically going to in term of the Nano
log collection right so these all three
component means the first let me just
recap it so first if any new user is
going to start the google.com access
their traffic is good once they have to
send the TCP scene right so I'll discuss
in very detail TCP sync is going to be
sent by the user after authentication
that tcps in is going to be intercept by
the you know gen right G Square
enforcement node and this is also having
the component that is Central Authority
they will just check based on the
YouTube usual tcpc in what the policy
need to be imposed what the connection
ID need to be allowed how the different
different website or application need to
be allowed and then they will just force
um like they will just you know make the
connection from the Gen to the any
application whatever you want to do on
behalf of you and once they will get the
reply it is going to provide to reply to
the user so this is how it is going to
happen so I hope this control plane data
plane right or strategic plane we
understand
right now next we understand about uh
different different topic about the
packet forwarding method about this like
uh single scan and multiple access and
high ability in the next lecture so
thanks for watching have a great day






![Rogue Trader (Full Ewan McGregor Movie) | Real Drama [4k] image](https://i.ytimg.com/vi/0AzziTZ8QqA/default.jpg)